In today’s hyper-connected digital world, businesses rely on robust IT infrastructure to stay operational and competitive. But with increasing cyber threats and the need for seamless network performance, understanding the difference between a NOC and SOC becomes crucial for any organization. A Network Operations Center (NOC) and a Security Operations Center (SOC) are two pivotal components of modern IT management, each serving distinct yet complementary roles. While both monitor and manage aspects of an organization’s technology ecosystem, the difference between a NOC and SOC lies in their core focus areas: one prioritizes performance and availability, while the other zeroes in on protection against malicious activities.
As cyber-attacks grow more sophisticated think ransomware, data breaches, and state-sponsored hacking companies can’t afford to overlook either. According to industry reports, the global cybersecurity market is projected to reach trillions in value by the end of the decade, underscoring the urgency. But why differentiate? The difference between a NOC and SOC isn’t just semantic; it impacts how businesses allocate resources, respond to incidents, and ensure long-term resilience. In this blog, we’ll dive deep into what each center entails, highlight the key difference between a NOC and SOC, and explore scenarios where having both could be a game-changer for your operations.
Whether you’re an IT manager, a C-suite executive, or a tech enthusiast, grasping the difference between a NOC and SOC can help you make informed decisions. Let’s break it down step by step, starting with the fundamentals.
What is a Network Operations Center (NOC)?
To fully appreciate the difference between a NOC and SOC, we must first understand what a NOC is. A Network Operations Center, or NOC, is essentially the nerve center for an organization’s network infrastructure. It’s a centralized hub where IT professionals monitor, manage, and maintain the day-to-day operations of networks, servers, databases, and other critical systems. The primary goal of a NOC is to ensure high availability, optimal performance, and minimal downtime.
NOCs operate around the clock, often in a 24/7 environment, using advanced monitoring tools to track metrics like bandwidth usage, server load, and network latency. For instance, if a router fails or there’s a spike in traffic causing slowdowns, NOC technicians are the first responders. They perform routine maintenance, troubleshoot issues, and implement updates to prevent disruptions. Tools commonly used in NOCs include network management software like SolarWinds, Nagios, or PRTG, which provide real-time dashboards and alerts.
One key aspect that highlights the difference between a NOC and SOC is the NOC’s reactive and proactive approach to non-security-related issues. NOCs focus on service level agreements (SLAs), ensuring that uptime meets or exceeds contractual obligations often aiming for 99.99% availability. This involves capacity planning, where teams forecast future needs to scale infrastructure accordingly. In larger enterprises, NOCs might integrate with help desks to handle user-reported problems, escalating complex issues to specialized teams.
Historically, NOCs evolved from telecommunications control rooms in the 1970s, adapting to the internet boom. Today, with cloud computing and remote work, NOCs have become more sophisticated, incorporating AI-driven analytics to predict failures before they occur. For example, machine learning algorithms can detect anomalies in traffic patterns, allowing preemptive action.
But NOCs aren’t without challenges. Over-reliance on manual processes can lead to alert fatigue, where technicians drown in notifications. To combat this, modern NOCs emphasize automation, such as scripting for routine tasks. The difference between a NOC and SOC becomes evident here: while NOCs deal with “natural” disruptions like hardware failures or power outages, they don’t typically delve into threat hunting.
In terms of staffing, NOC roles often require certifications like CCNA (Cisco Certified Network Associate) or CompTIA Network+. Entry-level positions might involve monitoring dashboards, while senior engineers handle architecture design. Salaries vary, but in the US, NOC analysts earn around $60,000-$80,000 annually, reflecting the operational focus.
Ultimately, a well-run NOC keeps the lights on, ensuring business continuity. Without it, even minor glitches could cascade into major outages, costing companies millions. As we explore the difference between a NOC and SOC further, you’ll see how this operational backbone contrasts with security-centric defenses.
What is a Security Operations Center (SOC)?
Shifting gears to underscore the difference between a NOC and SOC, let’s examine the Security Operations Center (SOC). A SOC is a dedicated facility or team focused exclusively on cybersecurity. Its mission is to detect, analyze, respond to, and mitigate threats that could compromise an organization’s data, systems, or intellectual property. Unlike a NOC, which ensures smooth operations, a SOC acts as a digital fortress, constantly vigilant against adversaries.
SOCs employ a multi-layered approach, starting with continuous monitoring of endpoints, networks, and applications for suspicious activities. Tools like SIEM (Security Information and Event Management) systems such as Splunk or IBM QRadar aggregate logs from various sources, using rules and machine learning to flag potential incidents. When an alert triggers, SOC analysts investigate, determining if it’s a false positive or a real threat like malware infection or unauthorized access.
The difference between a NOC and SOC is stark in their response protocols. SOCs follow frameworks like NIST’s Incident Response lifecycle: preparation, identification, containment, eradication, recovery, and lessons learned. For example, in a phishing attack, a SOC might isolate affected machines, reset credentials, and deploy patches across the network.
SOCs come in various models: in-house, managed (outsourced to MSSPs like Secure Works), or hybrid. In-house SOCs offer full control but require significant investment think dedicated rooms with video walls displaying threat maps. Managed SOCs, on the other hand, provide expertise without the overhead, ideal for SMEs.
A critical element in the difference between a NOC and SOC is the skill set. SOC personnel often hold certifications like CISSP (Certified Information Systems Security Professional) or CEH (Certified Ethical Hacker). They specialize in threat intelligence, forensics, and compliance with regulations like GDPR or HIPAA. Roles range from Tier 1 analysts (triage alerts) to Tier 3 hunters (proactive threat seeking).
Challenges in SOCs include the sheer volume of threats; cybersecurity incidents rose by 78% in 2023 alone, per reports. To address this, SOCs integrate SOAR (Security Orchestration, Automation, and Response) tools to automate workflows, reducing response times from hours to minutes.
Moreover, SOCs emphasize threat hunting proactively searching for hidden dangers using tools like Endpoint Detection and Response (EDR) platforms from CrowdStrike or Carbon Black. This proactive stance differentiates them from NOCs, which are more about maintenance than defense.
In essence, a SOC safeguards against the evolving landscape of cyber risks, from insider threats to advanced persistent threats (APTs). Without a SOC, organizations are blind to vulnerabilities, risking data loss and reputational damage. As we delve into the core difference between a NOC and SOC, these distinctions will become even clearer.

Key Differences Between a NOC and SOC
Now that we’ve covered the basics, let’s zoom in on the difference between a NOC and SOC. While both centers operate in real-time and use monitoring tools, their objectives, processes, and outcomes diverge significantly. Understanding this difference between a NOC and SOC can help organizations optimize their IT strategies.
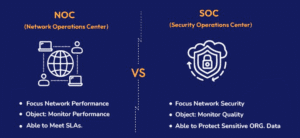
First, focus areas: A NOC is all about network performance and reliability. It deals with issues like bandwidth bottlenecks, hardware malfunctions, or software bugs that affect uptime. In contrast, a SOC targets security threats, such as viruses, DDoS attacks, or data exfiltration. This difference between a NOC and SOC means NOCs prevent operational downtime, while SOCs avert security breaches.
Second, tools and technologies: NOCs rely on network monitoring solutions that track metrics like packet loss or CPU utilization. SOCs, however, use security-specific tools like intrusion detection systems (IDS), firewalls, and vulnerability scanners. The difference between a NOC and SOC in tooling reflects their mandates performance dashboards versus threat intelligence feeds.
Third, team expertise: NOC staff are network engineers skilled in routing, switching, and cloud management. SOC teams comprise security analysts proficient in encryption, ethical hacking, and compliance. This skill gap underscores the difference between a NOC and SOC; one requires operational know-how, the other demands threat expertise.
Fourth, response times and priorities: NOCs adhere to SLAs, resolving issues based on severity e.g., critical outages get immediate attention. SOCs operate on a threat-based model, prioritizing incidents by risk level, such as containing a ransomware attack before it spreads. The difference between a NOC and SOC here is in the nature of “emergencies”: operational vs. existential threats.
Fifth, metrics for success: NOCs measure success through uptime percentages, mean time to repair (MTTR), and user satisfaction. SOCs track detection rates, incident response times, and compliance scores. This quantitative difference between a NOC and SOC highlights their distinct contributions to business health.
Operationally, NOCs often integrate with IT service management (ITSM) frameworks like ITIL for change management. SOCs align with cybersecurity standards like ISO 27001, emphasizing risk assessment. In terms of structure, NOCs might be more hierarchical, with clear escalation paths, while SOCs foster collaboration for rapid threat sharing.
Another layer to the difference between a NOC and SOC is their approach to incidents. A NOC might view a sudden traffic surge as a performance issue, whereas a SOC could investigate it as a potential DDoS attack. This overlap is where confusion arises, but the core difference between a NOC and SOC remains: prevention of downtime versus protection from malice.
Cost-wise, setting up a NOC involves investments in monitoring hardware, while SOCs require expensive security software and ongoing threat intel subscriptions. However, the ROI differs; NOCs save on lost productivity, SOCs on breach remediation costs, which average $4.45 million per incident globally.
In hybrid environments, the difference between a NOC and SOC blurs slightly with shared tools, but their missions stay separate. For instance, both might use AI for anomaly detection, but NOCs apply it to efficiency, SOCs to threats.
To illustrate, consider a telecom company: Its NOC ensures call quality and network coverage, while the SOC protects customer data from hacks. Ignoring the difference between a NOC and SOC could lead to siloed operations, missing holistic oversight.
In summary, the difference between a NOC and SOC is multifaceted, spanning goals, tools, skills, and metrics. Recognizing these can prevent resource misallocation and enhance overall resilience.
Why You May Need Both a NOC and SOC
Having dissected the difference between a NOC and SOC, the question arises: Why might your organization need both? In an era where digital transformation accelerates, relying on one alone could leave gaps. The synergy between them addresses both operational efficiency and security, creating a comprehensive defense.
First, complementarity: A NOC keeps systems running smoothly, but without a SOC, vulnerabilities go unchecked. Conversely, a SOC secures assets, but network failures could hinder its effectiveness. By having both, you cover the full spectrum the difference between a NOC and SOC becomes a strength when integrated.
For large enterprises, both are essential. Take a financial institution: The NOC manages transaction processing networks for speed, while the SOC thwarts fraud attempts. Without both, either performance dips or security falters, risking customer trust.
SMEs might outsource: Managed NOCs handle routine monitoring, freeing internal teams for core business, while MSSPs provide SOC services affordably. This dual approach mitigates the difference between a NOC and SOC by leveraging external expertise.
Integration benefits: Modern setups often co-locate NOCs and SOCs or use unified platforms like next-gen SIEMs that blend network and security data. This reduces silos, enabling faster incident correlation for example, a NOC alert on unusual traffic could trigger SOC investigation.
Cost justification: While dual centers seem expensive, the combined ROI is high. NOCs minimize downtime costs (estimated at $5,600 per minute for enterprises), and SOCs avert breach expenses. In regulated industries like healthcare, compliance demands both to meet standards like HIPAA.
Challenges of not having both: Organizations with only a NOC might overlook insider threats, while SOC-only setups could ignore performance issues masking attacks. The difference between a NOC and SOC, if not bridged, exposes blind spots.
Case study: During the 2021 Colonial Pipeline hack, a SOC could have detected the ransomware early, but integrated NOC oversight might have isolated networks faster, minimizing disruption.
Future trends: With IoT and 5G, threats multiply, making both indispensable. AI integration will further blur lines, but the core difference between a NOC and SOC persists.
In short, needing both stems from the holistic nature of IT risks. Assess your needs: If uptime and security are non-negotiable, invest in both.
Conclusion
In wrapping up, the difference between a NOC and SOC is fundamental to robust IT management. A NOC ensures operational excellence, a SOC fortifies against threats, and together, they provide unbeatable resilience. Whether building in-house or outsourcing, understanding this difference between a NOC and SOC empowers better decisions. In a threat-laden world, having both isn’t a luxury it’s a necessity for sustained success.
Elevate Your IT with vGics Global: Secure, Scalable, Unstoppable
In a world where cyber threats lurk around every corner and downtime can cost thousands per minute, your business deserves more than just IT support it needs a fortress. At vGics Global, ISO 27001:2022 certified experts in SOC and NOC services, we deliver 24/7 monitoring, cloud mastery, and cybersecurity that lets you focus on growth, not glitches.
Ready to transform your infrastructure? Partner with vGics Now – Schedule your free risk assessment today and unlock enterprise-grade protection tailored for SMBs like yours. Don’t wait for the next breach build resilience with us. Your secure future starts here!